The Peking duck scam that happened in Singapore a few days ago is a very unfortunate and sad incident that shows how scammers exploit people’s trust. According to the news reports by The Straits Times [1], the elderly man was lured by a Facebook ad from a supplier called "Xiao Xiao Ya Zi" that offered 1.5kg of Peking duck for only S$23.80, with an extra S$5 for delivery fees.
“I asked him: ‘Is this a scam?’ He said that no one would be cheated of S$5 and that this was a small thing. He told me that I had a lot of wisdom and experience. I agreed to proceed since this was a matter of only S$5,” [1]
 |
Here is what happened:
- The seller contacted him on WhatsApp and instructed him to download a third-party app called Grab&Go to place the order.
- He was then asked to make a S$5 deposit payment through PayNow, which is a mobile payment service in Singapore.
- However, as soon as he made the payment, his phone screen went black and restarted several times. He could not access any functions on his phone and was unable to call for help.
- The scammer assured him that that his order would be processed soon, and that all is normal.
- Meanwhile, the scammer had hacked into his phone and raised his transaction limit on his DBS and POSB bank accounts. The scammer then transferred about S$59,000 out of his current and savings accounts, and also obtained a credit advance of nearly S$11,000 using his DBS credit card.
His wife noticed something was wrong and alerted their daughter, who then asked her brother to call the bank to block their father’s account. But it was already too late. The elderly man lost almost S$70,000 in life savings in a matter of minutes.
“I couldn’t believe the news. I thought: Why am I so stupid? I was so angry at myself for being cheated of my life savings. My family is frustrated and I ended up quarrelling with my wife,”
| Bait, Hook, Catch |
|---|
 |
| i) BAIT: Scammers set up a fake ad on social media offering good deal ii) HOOK: Convince victim to download and install a malicious app iii) CATCH: Infect victim’s device, obtain credentials, gain permissions and siphon money out |
The Discussion
This is not the first time that scammers have used food delivery apps or websites to lure unsuspecting customers. In January 2023, the Singapore Police Force warned the public about a series of scams involving fake food delivery platforms that asked users to pay for their orders [2]. The scammers would then use the payment details to access the victims’ bank accounts and transfer money out. The police also alerted the public to the resurgence of phishing scams involving malware installed on victims’ Android phones. According to a report by Singapore's Police Force, more than 750 Android device users fell prey to malware scams in the first half of 2023, resulting in losses of more than S$7 million [3].
There are a few ways that scammers can take control of a mobile phone after a victim has made a small payment via a legitimate mobile payment service. One way is to use a remote access tool. Remote access tools allow someone to control another person's device remotely, including seeing their screen, interacting with apps, and transferring files. Scammers can trick victims into downloading and installing a remote access tool on their device by disguising it as another app, such as a fake mobile payment app or a security app.
Also, remote access tools can be used to install keylogging malware on a victim's device without their knowledge or consent. Once the keylogging malware is installed, it can record all of the user's keystrokes and send them back to the attacker. In August, the police force and the Cyber Security Agency of Singapore released a joint advisory in August to increase awareness about the growing frequency of malware scams impacting Android users [4]. Below is an illustration on the stagesof a typical malware attack.
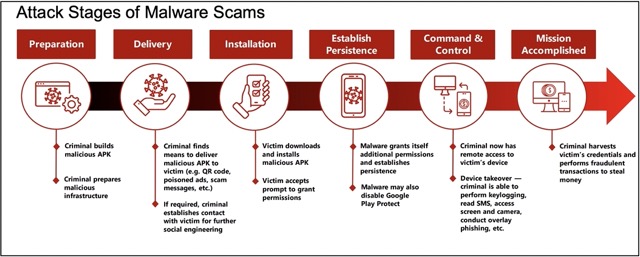 |
| Image Credit: Joint Advisory on Malware Scams Affecting Android Users [4] |
In the case of the Peking duck scam, the attacker may have used the remote access tool to install a keylogging malware on Mr. Loh's phone. The keylogging malware could then have recorded Mr. Loh's login credentials for his bank accounts, which the attacker could then use to steal his money. Here's a possible narration:
- Reconnaissance: The scammer then creates a fake ad offering a cheap deal on Peking duck, which is a popular dish in Singapore. That's the bait.
- Delivery: The scammer delivers the malware to the man’s phone by persuading him to download a third party app called Grab&Go from a dubious source. The app is disguised as a legitimate food delivery service, but it actually contains a keylogging spyware that can record the man’s keystrokes and send them to the scammer .
- Installation: The malware installs itself on the man’s phone by requesting permissions from him or by exploiting a vulnerability in his phone’s operating system or software. The malware also installs a keylogger that can capture the man’s passwords, usernames, bank account details, and other sensitive information .
- Execution: The malware executes its malicious functions, such as stealing the man’s data, sending commands to his phone, or launching further attacks on other devices or networks. The malware also uses the man’s PayNow account to make a \$5 deposit payment, which triggers the phone screen to go black and reboot repeatedly.
- Persistence: The malware maintains its presence on the man’s phone, either by hiding itself from detection or by resisting removal. The malware also updates itself with new features or capabilities adn grants itself permissions.
- Exfiltration: The malware sends the stolen data to the scammer’s server or another destination. The scammer then uses the data to access the man’s bank accounts and credit card and transfers his money .
Now, PayNow is a secure and convenient mobile payment service that allows users to transfer funds between different banks using their phone numbers, NRIC/FIN numbers,Scan PayNow QR or Virtual Payment Address (VPA). It adopts the same high security standards adopted by the Singapore banking industry for funds transfer including FAST and GIRO. However, PayNow itself does not provide any security protection for the user’s device or data. Therefore, if the user’s device is infected by malware or hacked by scammers, it is likely that PayNow transactions can be compromised as well.
Furthermore, legitimate mobile payment services will not have access to the phone's operating system or your bank accounts. If a payment is made via a legitimate mobile payment service, the service will simply transfer the money from the bank account to the merchant's bank account. The service will not be able to take control of the payer's phone or see the payer's bank account information.
Safeguards
- Isolate the device: Turn on flight mode and Wi-Fi to disconnect the device from the internet and other devices to prevent the malware from spreading.
- Delete the app: Remove the malicious app from the device to prevent further harm.
- Scan your device: Use a trusted and legitimate anti-malware/anti-virus software to scan and remove the malware from the device.
- Check for unwarranted transactions on another device and continue to monitor the accounts: Check for any unauthorized transactions on other devices and continue to monitor the accounts for any suspicious activity.
- Change your passwords for online accounts: Use strong and unique passwords for all accounts and enable two-factor authentication to add an extra layer of security.
- Notify banks: Inform the banks about the unauthorized transactions and seek their assistance in recovering the lost funds.
Some banking apps offer a kill switch feature that allows the account holder to block or deactivate bank cards or online banking access if you suspect that you have been scammed. Kill switches are reactive tools that are designed to halt and delete all programs, documents, and log files created by the hackers to eliminate their digital footprint. It is a useful way to prevent further unauthorized transactions or access by the scammer.
However, a kill switch may not be able to protect you from transactions that have already been authorized by you. For example, the TrickBot banking Trojan has developed an Android app that can intercept one-time authorization codes sent to users' mobile devices, bypassing two-factor authentication for net banking services [5]. Similarly, the Brata banking-fraud Trojan can activate a kill switch that performs a factory reset and wipes infected devices clean after draining bank accounts [6].
In the case of the Peking duck malware scam attack, a kill switch would not have been useful once the malware was installed on the victim's device and the transaction was authorized by the user through the malware
References
[1] S. Sim, 74-year-old man loses $70K after downloading third-party app to buy Peking Duck, https://www.straitstimes.com/singapore/74-year-old-man-loses-70k-after-downloading-third-party-app-to-buy-roast-duck (accessed Oct. 5, 2023).
[2] “Police advisory on e-commerce scams involving sale of food items,” Singapore Police Force, https://www.police.gov.sg/Media-Room/News/20230109_police_advisory_on_e-commerce_scams_involving_sale_of_food_items (accessed Oct. 5, 2023).
[3] "Police advisory on new variant of malware scams," Singapore Police Force, https://www.police.gov.sg/Media-Room/News/20230920_police_advisory_on_new_variant_of_malware_scams (accessed Oct. 5, 2023)
[4] "Joint Advisory On Malware Scams Affecting Android Users", Singapore Police Force and Cybersecurity Agency of Singapore, https://www.csa.gov.sg/docs/default-source/publications/singcert/2023/joint-advisory-on-malware-scams-affecting-android-users.pdf?sfvrsn=3c5c66d5_1 (accessed Oct 5, 2023)
[5] P. Asinovsky , “Trickbot pushing a 2FA bypass app to bank customers in Germany,” Security Intelligence, https://securityintelligence.com/posts/trickbot-pushing-a-2fa-bypass-app-to-bank-customers-in-germany/ (accessed Oct. 5, 2023).
[6] D. Goodin, “Android malware can factory-reset phones after draining bank accounts,” Ars Technica, https://arstechnica.com/information-technology/2022/01/android-malware-can-factory-reset-phones-after-draining-bank-accounts/ (accessed Oct. 5, 2023).