Social psychologists excel at studying narrow, precise slices of psychological phenomena, but we struggle at the task of integrating disparate research findings to better understand complexities such as human conflict. K.M.Frost, 2021

Social media platforms have inadvertently become a store of insights, interactions, and, unfortunately, opportunities for cyber threats. Originally designed for communication and interactions, it has now become a source of many incidents such as data collection, targeted advertising, cyber bullying, phishing, scams and so forth. I have earlier discussed some of these such as: job scams, nft scams and in this pig butchering article, I outlined how psychology is a technology for persuasion and also the role of security awareness and habituation. As cybercriminals increasingly exploit the human element in their nefarious endeavors, I posit that the fusion of mimetic analysis with the cybersecurity can be a potent safeguard.
Social media mimetic analysis dives deep into the currents of human behavior, decoding the patterns and trends that govern our interactions in the virtual sphere. Its relevance to cybersecurity is akin to deciphering the language of digital deception and trust.
This article explores the symbiotic relationship between social media and mimetic analysis, unveiling its pivotal role in fortifying cyber defenses. This article discusses how social media mimetic analysis can assist in identifying social engineering attacks, and safeguard online reputations. However, as with any potent tool, it brings forth ethical considerations that demand careful navigation.
This article does not aim to be a comprehensive reference but rather an introductory venture into the implications of social media mimetic analysis and its relevance in safeguarding our digital society.
Mimetic Behaviour
At the heart of mimetic analysis is the "Mimetic Theory of Desires". This theory, developed by the renowned French thinker René Girard, is the philosophical bedrock upon which mimetic analysis is built. It discusses the intricate dynamics of human imitation, desire, rivalry, and cultural evolution, offering deep insights into the underpinnings of our social behavior—both in the physical and digital worlds.
- Imitation as the Catalyst:
Mimetic Theory posits that human beings are fundamentally imitative creatures. We learn and navigate the world around us by imitating the desires and behaviors of others. This imitation is the catalyst that drives human interaction and shapes our cultural norms.
- The Nature of Desire and Rivalry:
Girard's theory suggests that individuals often desire what others desire, creating a web of competition and conflict. In the digital realm, this manifests as the pursuit of likes, shares, and followers, with social media platforms serving as arenas for symbolic rivalry.
The "scapegoat mechanism" posits that societies often find relief from internal conflicts by collectively blaming and sacrificing a chosen scapegoat. In the digital sphere, this may be seen in online mob behavior, where individuals or groups are targeted with blame or condemnation.
| A break down on the psychology of mimesis. It starts with desire, moves to imitation, arousal of desires, all within a network of manipulated relationships |
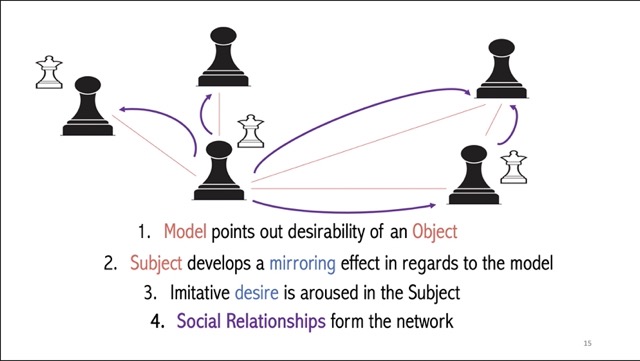 |
Understanding Mimetic Analysis
Mimetic analysis is a method of applying mimetic theory to various domains, such as literature, psychology, anthropology, and sociology.
Mimetic analysis, as an application of Mimetic Theory, enables experts to examine the intricacies of human behavior on social media platforms, deciphering the desires, rivalries, and imitative patterns that may be leveraged by cybercriminals. Incorporating Mimetic Theory into mimetic analysis adds depth and nuance to the understanding of social media dynamics and cyber threats.
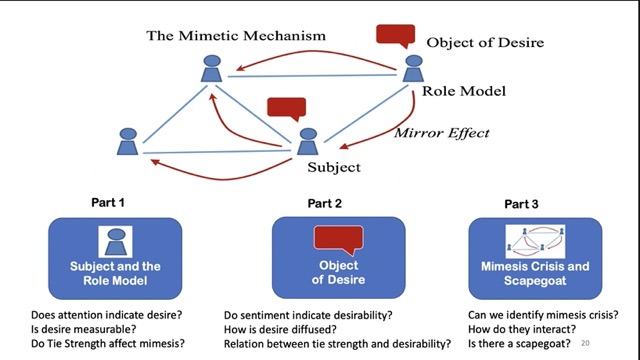
Imagine this:
On a social media platform, an individual shares a seemingly innocuous piece of information, perhaps a personal anecdote or a trending news article. What follows is a series of actions like reactions, shares, and comments, each interaction potentially setting off a cascade of imitations. This mimetic ripple effect can be benign, creating viral memes and trends, or malevolent, as in the case of the spread of disinformation, mal-information, or social engineering attacks.
Mimetic Analysis is the study of these patterns of imitation, influence, and behavior on social media platforms. It seeks to answer questions such as:
- How do certain ideas or behaviors gain traction and become viral phenomena?
- What motivates individuals to share specific content or engage with particular online communities?
- How do malicious actors exploit mimetic behavior to deceive, manipulate, or compromise the security of individuals and organizations?
One can then decode the mechanisms driving trends, uncover hidden vulnerabilities, and detect early warning signs of threats that may otherwise remain concealed.
What can we learn from Mimetic Theory and its relevance to Social Engineering?
Social engineering is a technique where cybercriminals exploit the innate human tendency to trust and mimic others, making it a potent threat in the cybersecurity landscape.
Mimetic analysis can help us understand the role of imitation and desire in human behavior and culture by examining the triangular relationship between the social engineer (S), the target (T), and the desired object (O). According to the Mimetic theory, S does not desire O directly, but rather imitates the desire of a mediator (M), who can be a person, a group, or an ideology. M endows O with value and attractiveness, and S tries to obtain O by influencing or deceiving T.
For example fake news is a type of social engineering attack [1] that involves spreading false or misleading information through various media platforms, such as websites, blogs, social networks, or messaging apps. The goal of fake news is to influence the opinions, beliefs, or actions of the public or specific groups, such as voters, consumers, or activists. A mimetic analysis of fake news can reveal how the attackers use mediators and objects of desire to manipulate the targets. For example, suppose an attacker (S) wants to sway the outcome of an election (O) in favor of a certain candidate or party. S can create and disseminate fake news stories that portray a rival candidate or party (M) as corrupt, incompetent, or dangerous. T may be influenced by M’s desire for O and decide to vote against M or abstain from voting.
Mimicking Trustworthiness
Social engineers excel at mimicking trustworthiness. They craft messages, profiles, and personas that appear genuine and authoritative. Understanding mimetic behavior is paramount in recognizing when trust is being exploited.
Deceptive Mimicry
Cybercriminals leverage the mimetic tendencies of individuals to mimic behaviors they perceive as normal or safe. By blending into the digital crowd, they avoid raising suspicion, making their malicious actions difficult to detect.
The Power of Imitation
The essence of mimetic behavior lies in imitation. Social engineers exploit this by imitating trusted entities or individuals. By mirroring the behavior and language of respected figures or institutions, they gain access to sensitive information or convince targets to take harmful actions.
Emotional Manipulation
Beyond imitation, social engineering often involves the manipulation of emotions. Understanding the emotional triggers that lead to sharing sensitive information or clicking on malicious links is central to thwarting these attacks.
Mimetic Analysis as a Defense
Applying mimetic analysis to social engineering detection is akin to decoding the choreography of manipulation. It involves scrutinizing communication patterns, identifying unusual imitative behavior, and recognizing emotional cues that may signal a social engineering attempt.
Anonymity and Scapegoating
Social engineers may exploit the anonymity provided by social media platforms. They can also orchestrate digital scapegoating by creating false narratives that rally individuals against a common target. Recognizing these dynamics is essential to prevent manipulation.
Education and Awareness
Beyond technical defenses, education plays a pivotal role. By teaching individuals about the mimetic nature of social engineering and the tactics employed by cybercriminals, we empower them to become less susceptible to manipulation.
Ethical Implications:
The intersection of social engineering and mimetic analysis also raises ethical questions. Ethical hacking practices, responsible disclosure, and respect for privacy are vital considerations in the quest to protect against social engineering attacks. Social engineering is an art of deception that thrives on mimetic behavior. It relies on the age-old human tendency to trust, imitate, and seek connection. By incorporating mimetic analysis as a core defense strategy, cybersecurity professionals can unravel the patterns of manipulation, recognize the masquerade of trustworthiness, and fortify the digital world against the subtle and pervasive threat of social engineering. Understanding the mimicry that fuels these attacks can assit in identifying the threat actorts choreography of deception.
References
[1] Sjouwerman, S. (2022), Scam Of The Week - Fake News: a Content-based Social Engineering Attack Available at: https://blog.knowbe4.com/scam-of-the-week-fake-news-a-content-based-social-engineering-attack